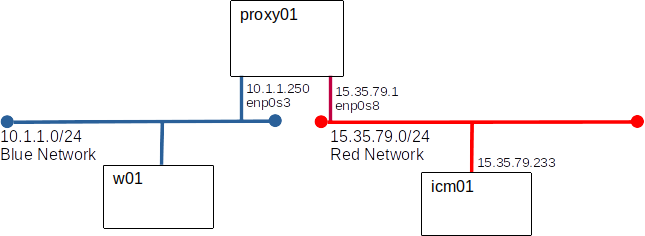
Not all servers are equally secure or equally trusted. Today we will us a transparent proxy to isolate a system we don't quite trust.
Rocky found a cool old internet connected coffee maker at the thrift store. We would really love to put it on our network, but there are some problems we need to address.
Here's what we know about the coffee maker:
We will use a transparent proxy to expose only port 80 on our blue network.

curl http://15.35.79.233
Our current configuration is usable but awkward. Users must log on to prox01 to access icm01. It would be much more convenient if we could access icm01 directly from any node on blue.
systemctl disable firewalld.service systemctl stop firewalld.service systemctl mask firewalld.service
net.ipv4.ip_forward=1
cat > /etc/sysconfig/nftables.conf <<EOF
table inet my_inet_table {
}
EOF
systemctl enable nftables.service systemctl start nftables.service
nft list tables
nft list table inet my_inet_table
Remember to run systemctl reload nftables.service to reload the rules after edits.
These rules will apply only to packets destined for proxy01. Packets that are being routed through proxy01 are not subject to these rules.
Note: Check our work after each step by trying 'something that should work' and 'something that should not work' after each change.
table inet my_inet_table {
chain input {
# declare new chain named filter hooked to the input entry point and set default policy to drop
type filter hook input priority 0; policy drop
}
}
chain input {
type filter hook input priority 0; policy drop;
# allow ssh
tcp dport ssh accept
}
chain input {
type filter hook input priority 0; policy drop
ct state established,related accept
# allow new tcp connections to port 22 (ssh)
tcp dport ssh ct state new accept
}
curl http://localhost
chain input {
type filter hook input priority 0; policy drop
ct state established,related accept
tcp dport ssh ct state new accept
# allow any packet if it is being sent to the look back interface
iif lo accept
}
# on proxy01 try... curl http://localhost
chain input {
type filter hook input priority 0; policy drop
ct state established,related accept
# allow new ssh packets that came in on enp0s3 (blue)
iif enp0s3 tcp dport ssh ct state new accept
iif lo accept
}
chain input {
type filter hook input priority 0; policy drop
ct state established,related accept
# allow new ssh packets that came in on enp0s3 (blue)
iif enp0s3 tcp dport ssh ct state new accept
# allow any packet if it is being sent to the look back interface
iif lo accept
# accept all icmp packets (v4 and v6)
ip protocol icmp accept
ip6 nexthdr icmpv6 accept
}
The packets we proxy will pass through us like they were routed. We want to let these packets through but no others.
chain forward {
type filter hook forward priority 0; policy drop;
# required for stateful rules
ct state established,related accept
# allow http
tcp dport 80 ct state new accept
# accept all icmp packets (v4 and v6)
ip protocol icmp accept
ip6 nexthdr icmpv6 accept
}
We will us Network Address Translation to automatically forward packets destined to 10.1.1.250:80 to 15.35.79.233:80 and to make sure the response packets can find their way back.
table ip nat {
chain postrouting {
type nat hook postrouting priority srcnat; policy accept;
# make sure proxied packets can find their way home
#
oif "enp0s8" tcp dport 80 log snat to 15.35.79.1
}
chain prerouting {
type nat hook prerouting priority dstnat; policy accept;
# re-address http packets to icm01
#
iif "enp0s3" tcp dport 80 dnat to 15.35.79.233
}
}
curl http://10.1.1.250
We have a working proxy but we should make it a bit more secure.
tar cf ~/nftables_good.tar /etc/sysconfig/nftables.conf
Submit your nftables.conf to Canvas