Overview:
Today you will built a web server, similar to the one you built for Evaluation 1, but it will be more secure.
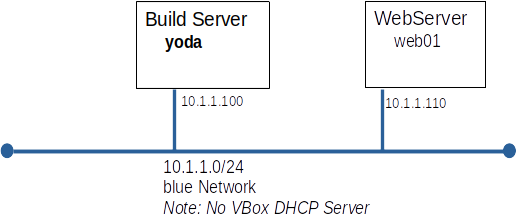
Part A: Build and Patch web01
- Build on the blue network.
- Patch from the YUM repos on yoda.
- Make sure that web01 only looks to yoda for YUM repos.
- Set static IP addresses
- Set static hostname
- Add yoda and web01 to /etc/hosts on web01
- Install Apache (httpd) on web01
- Configure Apache to start automatically
- No firewall configuration is required.
Part A and 3/4: Install the HandsOnEval.tar archive
This is a good opportunity to check if web01 is build more or less correctly. We will install the HandsOnEval02.tar archive in root's home directory on web01.
- Download HandsOnEval02.tar from Canvas
- Expand the archive on web01, as root.
- root's home should now contain:
./HandsOnEval02/alice.pub ./HandsOnEval02/bullwinkle_msg_1.txt ./HandsOnEval02/bullwinkle_msg_2.txt ./HandsOnEval02/bullwinkle_msg_3.txt ./HandsOnEval02/bullwinkle_msg_4.txt ./HandsOnEval02/bullwinkle.pub.txt ./HandsOnEval02/HostInfo02.sh ./HandsOnEval02/rocky.pub ./HandsOnEval02/trojan_c
- try running HostInfo02.sh
Part B: Instructions from Bullwinkle
- Use the default version of GPG to check the validity of the messages from Bullwinkle found in HandsOnEval02.tar
- Execute all the valid instructions. Note: Bullwinkle gets user_name and UID confused.
Part C: Install Rocky and Alice's ssh keys
Your team leader, Rocky, likes to be able to log onto ever server without typing a password. Alice will be managing web01 and should be able to log in without a password as well. Furthermore, since Alice is on vacation, Rocky will need to be able to log in as Alice or himself. All the keys you need can be found in the evaluation tar archive.
- Create two users: rocky and alice
- Using Rocky's public key (rocky.pub) configure ssh so that rocky can log on without typing a password.
- Using Rocky's public key (rocky.pub) configure ssh so that rocky can log on as alice without typing a password.
- Using Alice's public key (alice.pub) configure ssh so that alice can log on without typing a password.
Part D: trojan_c analysis
- Build an IDS to track changes to all executables and the contents of /etc
- Run trojan_c
- Create a text file, /tmp/answers.txt, describing what trojan_c does.